shopping online and recreational fields.
Artificial Intelligence: A Key Player in Personalization
Artificial intelligence significantly contributes to improving tailoring within context-sensitive suggestion engines. Through examining large datasets, AI algorithms can spot trends and patterns that direct user behavior.
Artificial intelligence significantly enhances personalization in recommendation systems by analyzing data to uncover user preferences.
This innovation allows for the distribution of tailored content, products, or features based on user behavior, situational context, and historical interactions. Adaptive learning models persistently evolve with fresh insights, increasing the relevance of recommendations over time.
Moreover, AI facilitates real-time analysis, allowing for quick changes based on audience participation and external variables. Through these capabilities, smart technology transforms basic solutions into individualized services, ultimately driving customer contentment and loyalty.
As a result, organizations taking advantage of AI for personalization can successfully meet the diverse needs of their audience, cultivating deeper connections.
Understanding User Preferences Through Keytalk
Keytalk employs refined algorithms to analyze user activity patterns, providing clarity into user preferences.
By learning these structures, the platform can adapt content delivery to increase user engagement.
Such a tailored method ensures that guidelines are suitable and timely, tailoring to the individual wishes of each user.
User Behavior Patterns
While users interact with digital platforms, their activity patterns reveal valuable insights into preferences and interests.
Keytalk leverages sophisticated analytics to monitor user interactions, such as clicks, duration spent on particular content, and ways users navigate. By analyzing these data elements, Keytalk uncovers insights and resemblances among visitors, helping to form a comprehensive profile of individual preferences.
This assessment not only points out well-liked features and material but also identifies hidden interests that may need addressing. By acknowledging evolution in behavior over time, Keytalk can adapt its strategies, ensuring that recommendations remain suitable and on time.
All things considered, understanding user behavior patterns facilitates Keytalk to enhance its approach, upgrading the overall user experience on digital platforms.
Individualized Content Delivery
To guarantee content resonates with users, individualized content delivery depends greatly on the assessment of user preferences. Keytalk harnesses innovative algorithms to process user data, letting the platform modify content in real time. This method ensures that users get pertinent recommendations that match their distinct interests and activities.
Keytalk studies preferences through several methodologies, including:
- History of User Interactions: Analyzing engagement metrics and click data.
- Demographic Insights: Factoring in age, geographic location, and gender.
- Content Consumption Patterns: Identifying frequently viewed topics.
- Feedback Collection Methods: Incorporating user reviews and feedback.
- Engagement on Social Media: Analyzing shares and likes for further insights.
Aspects Impacting Recommendations
Comprehending the multiple aspects that impact recommendations is vital for boosting the performance of AI-powered solutions. Several elements contribute to the quality of recommendations, including participant actions, preferences, and historical interactions.
Data about context, like the time of day, the location, and the device employed, greatly impacts tailored suggestions. Additionally, profiling data and peer influences can further refine the recommendations presented to users.
AI algorithms examine these variables to uncover trends and forecast user choices, ensuring that the suggestions continue to be relevant and prompt. The integration of broad data origins ultimately enhances the comprehensive user interaction, making the recommendations more personalized and successful in fulfilling unique needs.
Boosting User Interaction with Customized Recommendations
Bespoke advice can greatly enhance user engagement by delivering tailored information that resonates with specific preferences.
Utilizing contextual user insights, platforms can create experiences that hold greater relevance that attract attention and stimulate interaction.
This technique not only nurtures a greater connection with users but also raises the odds of continual engagement.
Individualized Content Delivery
As individuals explore the extensive online world, personalized content delivery is identified as a fundamental strategy for elevating engagement. By tailoring suggestions based on individual preferences and behaviors, platforms can greatly improve user satisfaction and loyalty.
This approach not only fosters deeper connections but also drives higher conversion rates.
Important factors in personalized content delivery consist of:
- User Interaction Insights: Monitoring user interactions to grasp preferences.
- Instant Recommendations: Delivering immediate recommendations centered on current trends.
- Group Segmentation: Dividing users based on interests to enhance content relevance.
- User Feedback Channels: Motivating users to provide feedback for improved suggestions.
- Advanced Learning Algorithms: Utilizing advanced analytics to predict user needs.
Collectively, these factors offer a more stimulating and meaningful experience that appeals to users.
Contextual User Insights
As consumer preferences determine how content is provided, contextual user insights improve the process of personalization by considering the context in which users interact with platforms.
This data encompass factors such as geographical position, hour of the day, type of device, and even social context, allowing for a more nuanced understanding of user activity. By analyzing this information, AI systems can generate customized suggestions that resonate with users in live scenarios, thereby increasing participation.
By way of example, a user browsing a travel site during their lunch break might receive destination suggestions that align with their immediate travel plans.
Hence, situational user insights bridge the gap between static preferences and adaptive user experiences, fostering enhanced relationships and boosting the chances of response to advised content.
Practical Uses of Keytalk's Innovations
The advancements from Keytalk has found a range of applications across different sectors, transforming how businesses engage with their patrons. By leveraging recommendations based on context, companies can enhance client experiences and drive business growth.
Several significant applications consist of:
- E-shop: Personalized shopping experiences based on user behavior and preferences.
- Tourism and Accommodations: Customized travel recommendations and itinerary planning for individual travelers.
- Medical Services: Customized treatment suggestions and treatment plans based on patient data.
- Entertainment: Personalized content suggestions for streaming services, improving viewer satisfaction.
- Bricks-and-Mortar Stores: Upgraded retail interactions through location-based promotions and offers.
These examples highlight Keytalk's capability to change customer interactions, making them highly pertinent and significant across a range of sectors.
Keytalk's innovations elevate customer engagement, confirming that interactions are both meaningful and beneficial in multiple industries.
The adoption of this technology signifies a shift towards a more personalized business landscape.
Perks of Using Contextual Recommendations
Context-specific recommendations deliver significant advantages by boosting the experience of users through individualized advice.
They facilitate personalization on a large scale, enabling companies to address individual preferences efficiently.
Therefore, this approach contributes to boosted interaction metrics as individuals come across more suitable content and offerings.
Enhanced User Experience
As users navigate through digital platforms, the ability to receive tailored recommendations based on their unique contexts greatly enhances their overall experience.
Context-aware recommendations enable a smooth interaction, confirming that users discover meaningful content quickly. This yields a more captivating and enjoyable user journey.
Key advantages include:
- Improved Relevance: Proposals are tailored to present demands and interests.
- Effective Use of Time: People reduce time in quest of fitting content.
- Better Engagement: Personalized recommendations foster deeper interactions.
- Higher Satisfaction: Users feel understood and valued by the platform.
- Enhanced Retention: Positive experiences encourage users to return frequently.
Scale Your Personalization
Amidst various digital platforms trying to give individualized interactions, achieving personalization at scale remains a considerable challenge.
Recommendations that are context-aware utilize artificial intelligence to analyze how users behave, preferences, and situational factors, enabling a tailored approach that adapts to user-specific desires. This technology allows for the delivery of relevant content and services, enhancing user satisfaction and loyalty.
By harnessing vast amounts of data, organizations can spot patterns that inform more informed decisions and recommendations. Consequently, businesses can reach a variety of customer segments more successfully, leading to increased conversion rates and customer retention.
In the end, the execution of adaptive suggestions creates a more dynamic user experience, connecting individual preferences and extensive application, resulting in a shift in how brands engage with their audiences.
Increased Engagement Rates
In what ways can organizations effectively boost audience involvement in an increasingly competitive digital landscape?
AI-powered suggestions powered by advanced algorithms serve as a strategic tool to enhance engagement with users. By providing specific recommendations based on how users behave and preferences, businesses can create a more engaging environment.
The positive aspects of these suggestions include:
- Enhanced user satisfaction by providing tailored content.
- Boosted conversion metrics since users encounter solutions that fit their needs.
- Boosted retention rates thanks to personalized engagements driving return customers.
- Improved brand loyalty stemming from positive user experiences.
- Increased awareness of consumer actions, providing opportunities for refined marketing plans.
Utilizing personalized suggestions can significantly enhance user engagement and foster business growth.
Keytalk's Algorithm: A Deep Dive
In the world of recommendations that understand context owing to its original way of uniting user interactions and environmental influences.
Utilizing machine learning approaches, the algorithm crunches live data, including placement, hour, and user inputs, to create tailored proposals. This dynamic adaptability allows Keytalk to develop its estimates repeatedly, enhancing user experience.
Also, the algorithm leverages collaborative filtering and content-based methods, ensuring a thorough understanding of user preferences. The result is a sophisticated system capable of delivering personalized recommendations that resonate with users on different facets.
The synthesis of collaborative filtering and content-oriented methods in the algorithm guarantees an in-depth comprehension of user preferences for personalized advice.
Keytalk’s emphasis on context not only improves accuracy but also fosters deeper engagement, making it a pivotal tool in the landscape of recommendation systems powered by AI.
Anticipated Trends in AI-Driven Personalization
The development of algorithms that are aware of context, for example, those utilized by Keytalk, establishes the foundation for future trends in personalization utilizing AI.
As technology advances, several key trends are likely to emerge:
- Refined User Profiling: Employing extensive insights into user habits and likes.
- Live Adaptation: Systems that modify suggestions in real-time based on current information.
- Comprehensive Interaction: Incorporating sound, text, and imagery for a fluid interaction.
- User Privacy Oriented Techniques: Aligning personalized solutions with user privacy assurance and data protection.
- Platform-Agnostic Synchronization: Ensuring cohesive recommendations across different devices and platforms.
These patterns reflect a movement towards more understandable and user-focused personalization, thereby enriching the overall experience for users.
Kickstarting Your Experience With Keytalk's Advice
Unveiling the power of Keytalk's recommendations requires knowing its innovative algorithm crafted to evaluate user context efficiently. This algorithm features an array of data factors, including user patterns, interests, and live scenarios, to deliver individualized proposals.
To begin, users need to incorporate Keytalk's API into their applications, allowing seamless data exchange. After installation, defining user profiles and setting preferences is essential for optimizing recommendations. Continuously refreshing these profiles boosts the algorithm's accuracy over the long term.
Additionally, leveraging analytics tools provided by Keytalk enables track engagement and refine recommendations further. By following these steps, businesses may exploit the power of smart recommendations, ultimately improving user experience and driving engagement.
Keytalk sets a fresh benchmark sets a new standard in bespoke interactions.
Frequently Asked Questions
In What Ways Does Keytalk Maintain User Data Privacy and Security?
The matter of how a company secures user customer data confidentiality and protection is crucial in today's digital age.
Keytalk utilizes advanced encryption methods to ensure the safety of sensitive information and follows strict data protection regulations.
Additionally, they implement routine security audits and use anonymization techniques to protect user identities.
Can I Customize My Recommendation Settings in Keytalk?
Are users able to personalize their experiences to match their tastes? In the domain of advisory systems, personalization is frequently a critical aspect.
Users are able to personalize their recommendation settings, allowing for a more personalized interaction. This flexibility enables people to modify the types of suggestions they receive, ensuring that the content suits their interests and needs.
At last, this level of customization enhances client contentment and engagement within the platform.
Can Keytalk Function on All Devices and Platforms?
One compatibility between Keytalk with various gadgets and frameworks constitutes an necessary aspect for possible users.
Generally, it is designed to work seamlessly across a wide range of OS and devices, including cell phones, tablets, and PCs.
That said, exact compatibility may hinge on the device's specifications and the software version.
Users are recommended to check the official documentation for detailed information regarding the platforms we support to guarantee full functionality.
Keytalk's Recommendation Update Frequency
The amount of updates concerning suggestions shifts utilizing the chosen systems and data employed.
In general, systems like Keytalk aim to modify their recommendations in real-time or at consistent intervals to guarantee significance. This may involve ongoing learning from user actions and likes.
Which Sectors Can Make Use of Keytalk's Context-Aware Suggestions?
Several fields can greatly improve through personalized suggestions, like retail, where customized shopping journeys enhance customer satisfaction.
Healthcare providers can implement tailored suggestions to enhance patient care and therapeutic alternatives.
Furthermore, the hospitality industry can improve guest experiences through personalized service suggestions.
Furthermore, education can take advantage of these insights to provide customized learning pathways for students, making the recommendations applicable across diverse fields that focus on user engagement and satisfaction.
Final Thoughts
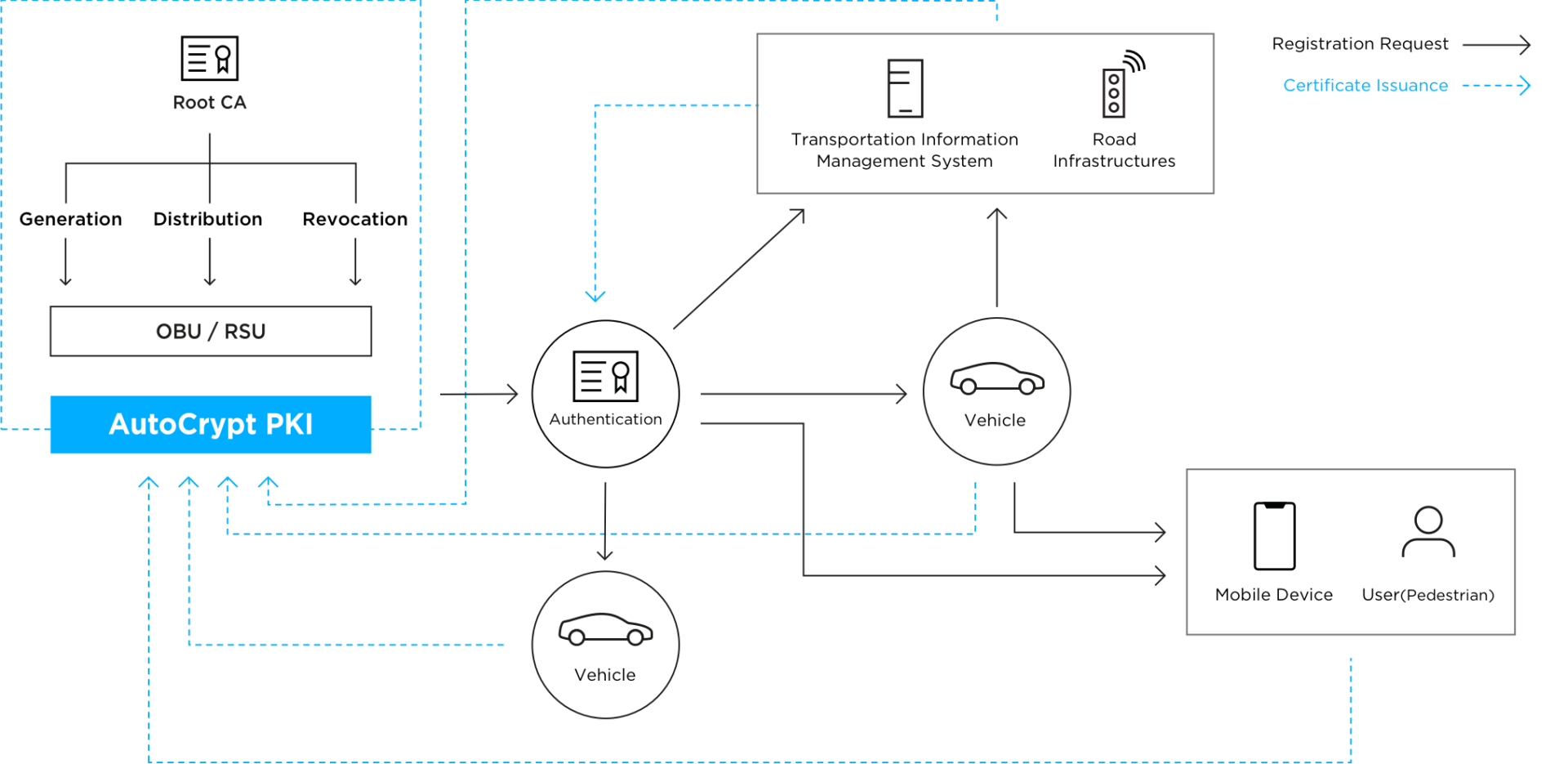
Amidst the evolving digital environment, Keytalk emerges as a lighthouse, guiding users through the fog of information with personalized insights. By harnessing the power of intelligent systems, it tailors suggestions that resonate deeply with personal tastes, much like a skilled artist who paints a unique portrait for each admirer. As the tides of tailored experiences continue to rise, Keytalk stands poised to illuminate pathways, enhancing PKI automation is essential for get more info securing digital progress. It streamlines the process of managing certificates, reduces manual errors, and enhances security for digital assets. Keytalk offers advanced solutions that facilitate smooth workflow automation and robust security systems. By integrating these solutions, organizations can improve command, visibility, and operational efficiency. This proactive approach not only mitigates risks but also positions businesses for sustainable growth. Discover how to leverage these pros further for enhanced digital evolution. Despite its seemingly complicated nature, Public Key Infrastructure (PKI) is crucial it is critical for ensuring the security of digital communications. Public Key Infrastructure (PKI) serves as a system for creating, managing, and distributing electronic certificates, which confirm the identities of users, devices, and services. Central to PKI is the dependence on asymmetric cryptography, involving two keys: a public key that is openly shared and a private key that remains confidential. This two-key system ensures data confidentiality and integrity during transmission. PKI encompasses various components, including Certificate Authorities (CAs) responsible for issuing certificates and Registration Authorities (RAs) that confirm identities. PKI automation is vital in today's digital environments by enhancing certificate handling procedures, ensuring organizations are able to manage their cryptographic needs efficiently. This automation improves security protocols by reducing human mistakes and keeping certificates current, thus safeguarding private data. Also, it contributes to reduced operating expenses, allowing businesses to manage resources more efficiently. Streamlined certificate management is essential for organizations seeking to enhance their digital security posture in an increasingly complex technological landscape. Smooth Digital certificate automation lets organizations to efficiently handle the lifecycle of certificates, minimizing risks and improving operational efficiency. Key benefits include: Bolstering security strategies is vital for entities working through the complexities of digital engagements. PKI automation is key in reinforcing a company's security framework. With the automation of the issuance, renewal, and revocation of online certificates, businesses can secure that their communications and transactions continue to be secure. This automation mitigates the threats from mistakes made by people and cuts down the potential for security vulnerabilities associated with manual processes. Additionally, PKI automation enables organizations to implement more secure authentication techniques, making sure that only authorized users gain access to sensitive information. As cybersecurity risks become increasingly sophisticated, embracing PKI automation not only strengthens security but also fosters trust among stakeholders, paving the way for a more trustworthy digital realm. Automating Public Key Infrastructure (PKI) not only improves security but also greatly reduces costs of operation for organizations. Through improving workflows and decreasing manual intervention, PKI automation offers various financial advantages: Incorporating PKI automation allows organizations to allocate resources more effectively, ultimately driving down operational expenses and supporting digital growth. Keytalk presents modern solutions that enhance certificate management, making it easier for organizations to handle their digital credentials. This improved security measures significantly bolster the integrity of these systems, ensuring protection against potential threats. As well , efficient workflow optimization improves processes, allowing businesses to focus on advancement and progress. Optimized certificate administration emerges as a critical component in the domain of cybersecurity, enabling organizations to proficiently control their cryptographic assets. Keytalk's state-of-the-art solutions minimize the difficulties of managing digital certificates, so that organizations can dedicate themselves to growth without jeopardizing security. Highlights of Keytalk's efficient certificate handling consist of: These innovations create a more nimble and protected internet environment, paving the way for optimized operational performance. Even though many companies attempt to boost their online security strategies, implementing robust security protocols remains an essential challenge. Keytalk addresses this issue through advanced solutions that fortify public key infrastructure (PKI) systems. By integrating cutting-edge secure encryption methods and access control methods, Keytalk guarantees that sensitive data remains protected against potential vulnerabilities. The solutions they offer are tailored to meet the needs of evolving security landscapes, adjusting to emerging threats and legislative demands. Additionally, Keytalk's innovative approach includes instant monitoring and incident response capabilities, enabling organizations to swiftly identify and mitigate vulnerabilities. This assertive measure not only safeguards digital assets but also fosters trust among stakeholders, thereby contributing to overall digital development in an increasingly interconnected landscape. Effective workflow automation represents a transformative approach for organizations seeking to enhance their operations. Keytalk’s cutting-edge solutions enhance workflows, guaranteeing a seamless integration of Public Key Infrastructure (PKI) into daily workflows. Through the use of automation, companies can realize: Such benefits empower organizations to improve productivity and emphasize strategic projects, fostering virtual development while maintaining a secure infrastructure. Keytalk demonstrates the capability of streamlined workflow processes for modern industry leaders. Overseeing digital certificates efficiently is necessary for ensuring security and credibility in internet transactions. Organizations face hurdles in handling a rising number of certificates across heterogeneous environments. Streamlining handling of certificates involves implementing systematic processes that simplify issuance, renewal, and revocation. A unified approach allows for better visibility and control, reducing the risk of certificates that have expired that can lead to service disruptions. Enhanced certificate management provides better control and awareness, decreasing the risk of expired certificates and preventing service breakdowns. By organizing certificates in terms of application and value, organizations can emphasize management tasks and utilize resources wisely. Merging with current IT systems boosts the full workflow, ensuring that each stakeholder is kept in the loop and aligned. In the end, efficient certificate handling not only enhances security but also supports organizational responsiveness in an increasingly tech-driven world. A significant portion of security issues stems from mistakes made by humans in certificate management procedures. Automated systems offers a robust solution to lessen these vulnerabilities by lowering human intervention. Employing automated systems allows, organizations can effectively lessen inaccuracies and boost efficiency. The advantages of automation consist of: As companies become more dependent on virtual assets for their operations, improving defensive strategies becomes paramount to protect sensitive information from evolving threats. Establishing strong security measures like encryption and multi-factor authentication reduces risks related to data compromises. Firms need to invest in ongoing surveillance and security analysis systems to recognize weaknesses ahead of exploitation. Periodic audits and compliance evaluations are vital to guarantee that security strategies are effective against evolving threats. In addition, team training on security awareness fosters a culture of vigilance, reducing the likelihood of human oversight. Keytalk empowers organizations to drive innovation and growth by streamlining their digital identity and access control systems. With the aid of progressive technologies, Keytalk elevates workflow efficiency and speeds up digital evolution. Organizations might anticipate the following rewards: Due to these strengths, Keytalk enables organizations to innovate and thrive in an ever-evolving digital environment, fostering sustainable expansion and business advantage. Different sectors can greatly benefit from Public Key Infrastructure automation, particularly the medical field, financial services, and the technology sector. Within healthcare, it provides secure patient data transfers, and the finance industry utilizes it for secure dealings and adhering to regulations. The technology domain utilizes PKI for securing communications and securing intellectual property. Moreover, sectors like government and telecommunications employ PKI automation to strengthen security protocols, streamline processes, and reinforce overall digital trust in their operations. Keytalk works harmoniously with established systems by implementing common protocols and APIs, enabling smooth communication and data interchange. This cohesiveness affirms that businesses can utilize Keytalk’s solutions without considerable upheaval to their usual workflows. Furthermore, its modular architecture supports growth, enabling businesses to tailor the integration to their specific needs. Through these features, Keytalk enhances overall system performance while maintaining a secure environment for digital growth and identity management. Implementing Keytalk products can be as intricate as assembling a complex puzzle. The cost fluctuates as per organizational size, specific requirements, and infrastructure compatibility. In general, firms ought to plan for expenses related to software permits, integration support, and continued support. Factors such as the extent of deployment and personalization also impact the overall investment. It's wise to undergo a detailed consultation to obtain a personalized quote that complies with the organization's individual aims and needs. It is possible to automate PKI personalized to fulfill unique organizational requirements. Various solutions provide configurational flexibility, allowing businesses to tailor the automation process tailored to their distinct security specifications, operational workflows, and regulatory standards. This configuration can enhance efficiency and effectiveness in managing digital certificates, ensuring that the PKI system aligns seamlessly with the organization's operational goals. In the end, the adaptability of the automation of PKI serves as an crucial asset for a range of use cases. At a moment when rotary phones are considered relics, the importance of post-implementation support should not be underestimated. Keytalk ensures significant support post-deployment of its solutions. This includes problem-solving, frequent updates, and user training to guarantee uninterrupted integration and functionality. Clients benefit from focused service teams prepared to tackle any concerns and enhance system performance, securing a smooth shift and ongoing success in their digital initiatives. To summarize, embracing PKI tech through Keytalk's innovative solutions not only elevates security but also drives significant advancements in digital technology. While some may argue that automation could introduce new complexities, the streamlined certificate management and reduction of manual errors ultimately create a more efficient and secure environment. By investing in advanced PKI tools, organizations can confidently navigate the digital landscape, ensuring their assets are protected while fostering innovation and growth in an increasingly competitive market.Maximize PKI Automation for Digital Success – Shielded by Keytalk
Essential Lessons
Grasping the Concept of Public Key Infrastructure (PKI)
The Significance of PKI Automation
Effortless Certificate Handling
Enhanced Security Measures
Streamlined Operational Expenses
State-of-the-Art Solutions by Keytalk
Hassle-Free Certificate Administration
Reinforced Protection Standards
Advanced Workflow Automation
Streamlining Certificate Management
Streamlining Processes to Reduce Manual Errors
Boosting Security Measures for Digital Assets
Propelling Growth and Innovation Using Keytalk
FAQ
What Industries Benefit Most From PKI Automation?
How Keytalk Connects to Existing Systems?
What Is the Price of Keytalk Solutions Implementation?
Can PKI Automation Be Customized for Specific Needs?
What Assistance Can Keytalk Provide After Implementation?
In Conclusion